Who Should Use OpenPGP
Throughout the history of PGP, and encryption in general, there have been countless critics promoting the theory that only those with something nefarious to hide have any reason to use such strong encryption. In fact, shortly after its initial development, Zimmermann found himself the target of an investigation by the US Government when PGP found its way outside the US, violating laws forbidding the export of such powerful encryption.
In point of fact, there are many reasons why a person should use encryption, especially in the context of digital communication. While many people think of email as something relatively private and secure, with few exceptions, nothing could be further from the truth. Email is more akin to a postcard than a private, sealed letter. Just as a postcard makes its way through multiple depots, post offices, mail trucks and individual hands—with its message plain to see—an email travels through a myriad of individual servers en route from the sender to the ultimate recipient. Along the way, an unscrupulous server operator could view the contents of such emails, with no way for the sender or recipient to know their privacy had been compromised. While this is of little concern when sharing a cute pet video, or your favorite new recipe, the stakes become much higher when it’s family members discussing financial issues or health concerns, an executive discussing an internal corporate policy, a programmer sharing source code with another developer, or any number of legitimate situations where it’s important to be able to communicate and share information, or even files, in a secure and private manner. It is just these kind of situations that makes OpenPGP an important tool for anyone concerned with privacy and security.
How It Works
At its core, OpenPGP is a public-key cryptography system. This kind of cryptography uses a public/private key-pair to encrypt and decrypt data. With public-key cryptography, once data is encrypted with a public key, only the corresponding private key can decrypt it. When you first install an OpenPGP client, you’re prompted to create a key-pair set and upload your public key to key servers, allowing people to search for it by your name or associated email address. In addition, OpenPGP also helps individuals to verify the authenticity and integrity of a message or encrypted file thanks to the included digital signature. Many software companies will include a PGP digital signature along with their software’s installer that customers can check to verify the integrity of a download, and help ensure it hasn’t been tampered with or compromised to include malicious code.
How to Use It
In spite of OpenPGP’s value, the one thing that has stymied its widespread adoption is ease-of-use. Like many powerful applications, its barrier-to-entry can sometimes be higher than many users want to deal with. While there are a myriad of OpenPGP clients—far more than the scope of this article can cover—the steps below should provide a general guide to installing and using OpenPGP.
Download a Client
When downloading an OpenPGP client, the first choice is deciding whether to download the commercial PGP from Symantec, or use one of the free, open source clients available. Generally, the commercial application offers the most streamlined and polished experience, with options for Mac, Windows and iOS, while the open source clients add support for Linux and Android, not to mention being free-of-charge.
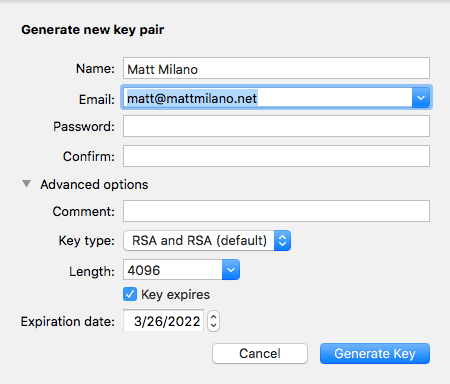
Create the Keys
The next step is to create your public/private keys . You will be asked for your name and email address, as well as the password you will enter encrypting and decrypting data.
While there are a couple of choices of algorithms to use for creating the keys, for most individuals, choosing the default RSA algorithm for both signing and encrypting is the best option. The larger the key, the stronger the encryption. As of the time of publication, 2048-bit keys had been factored, or hacked, although the resources required were well beyond practical application, making a 2048-bit key still viable for moderate security needs. Since a 4096-bit key is almost exponentially stronger than 2048-bit, a 4096-bit key is considered unhackable for the foreseeable future.
Upload the Key
Once your keys have been created, the next step is to upload your public key so other individuals can find it. Once your key is uploaded, anyone with a OpenPGP client will be able to search for your key based on your email address and use it to encrypt emails and files that only you can open. You can also directly email your public key to individuals you regularly communicate with so they can use it to encrypt files and emails destined for you.
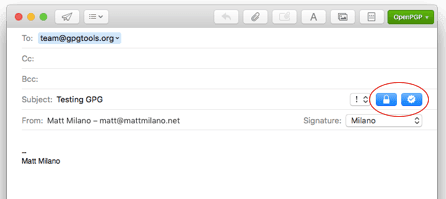
Integrate With Your Email Application
Since encrypting email is one of the fundamental uses for OpenPGP encryption, integration with your email program of choice is the next step. Many packages—such as GPG Suite by GPGTools—will automatically install a plugin for popular email clients, including Apple Mail, Microsoft Outlook or Mozilla Thunderbird. When emailing someone whose PGP key you possess, your OpenPGP software should give the option to encrypt and/or sign the email. Likewise, when receiving an email that has been encrypted using your public key, the software will prompt you to decrypt the message.
Without a doubt, OpenPGP encryption is a powerful tool for consumers and professionals alike. Although the learning curve may be a little steeper than many people are accustomed to, the benefits are well worth it. Whether a journalist working in a dangerous environment, a businessman discussing sensitive internal policy, developers sharing code or family members emailing each other private information, OpenPGP provides its users the peace-of-mind that comes with near military-grade encryption.